
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
How to set up the Two-Step Authorization (Google Authenticator). – Gaijin Support
Two-Factor Authentication – Arctic Reservations Support
How to set up the Two-Step Authorization (Google Authenticator). – Gaijin Support

Storing Two-Factor Codes - Enterprise Guide

Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
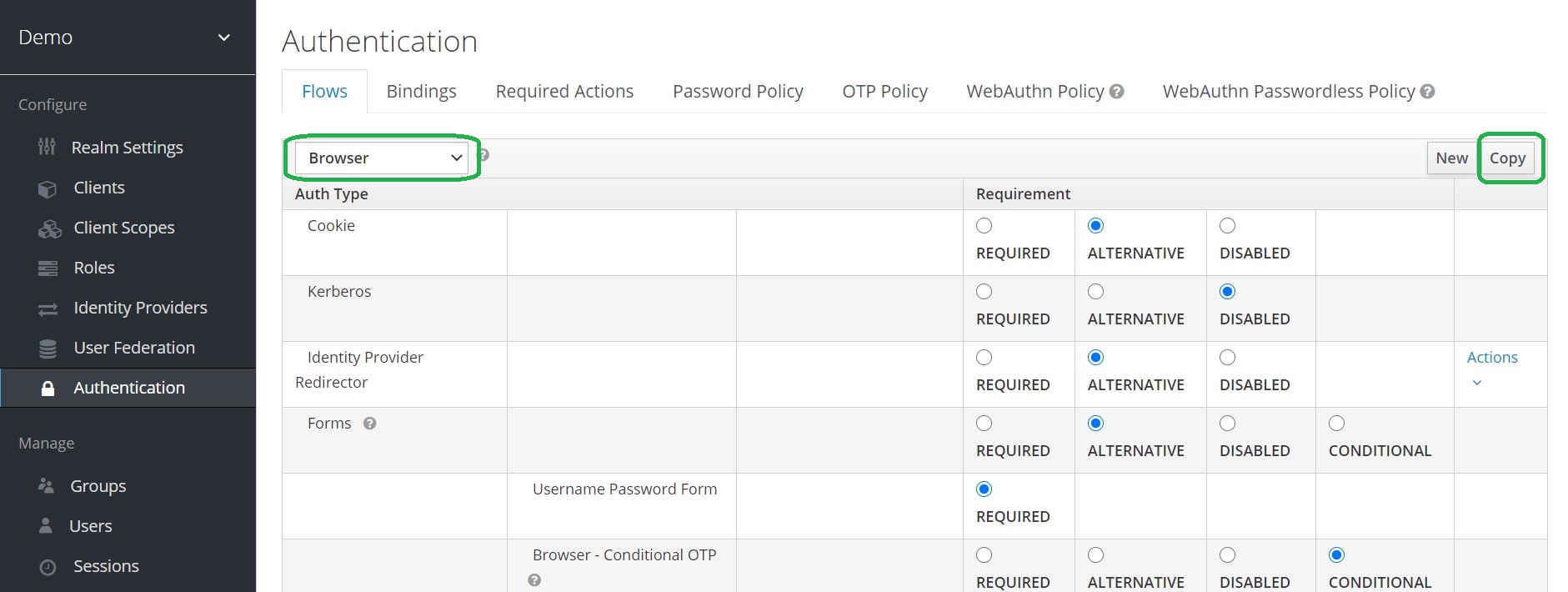
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog
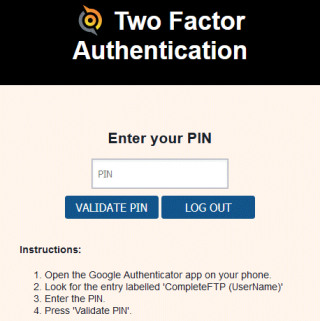
Two Factor Authentication (2FA) - EnterpriseDT
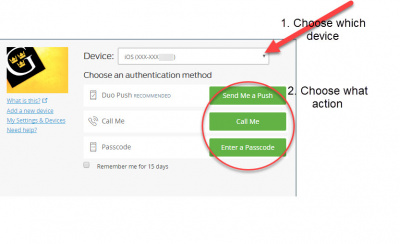
Duo Two Factor Authentication

Client to Authenticator Protocol (CTAP)
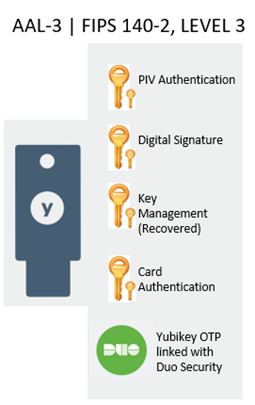
YubiKey FIPS + Duo Multi-Use Authentication Token - CyberArmed
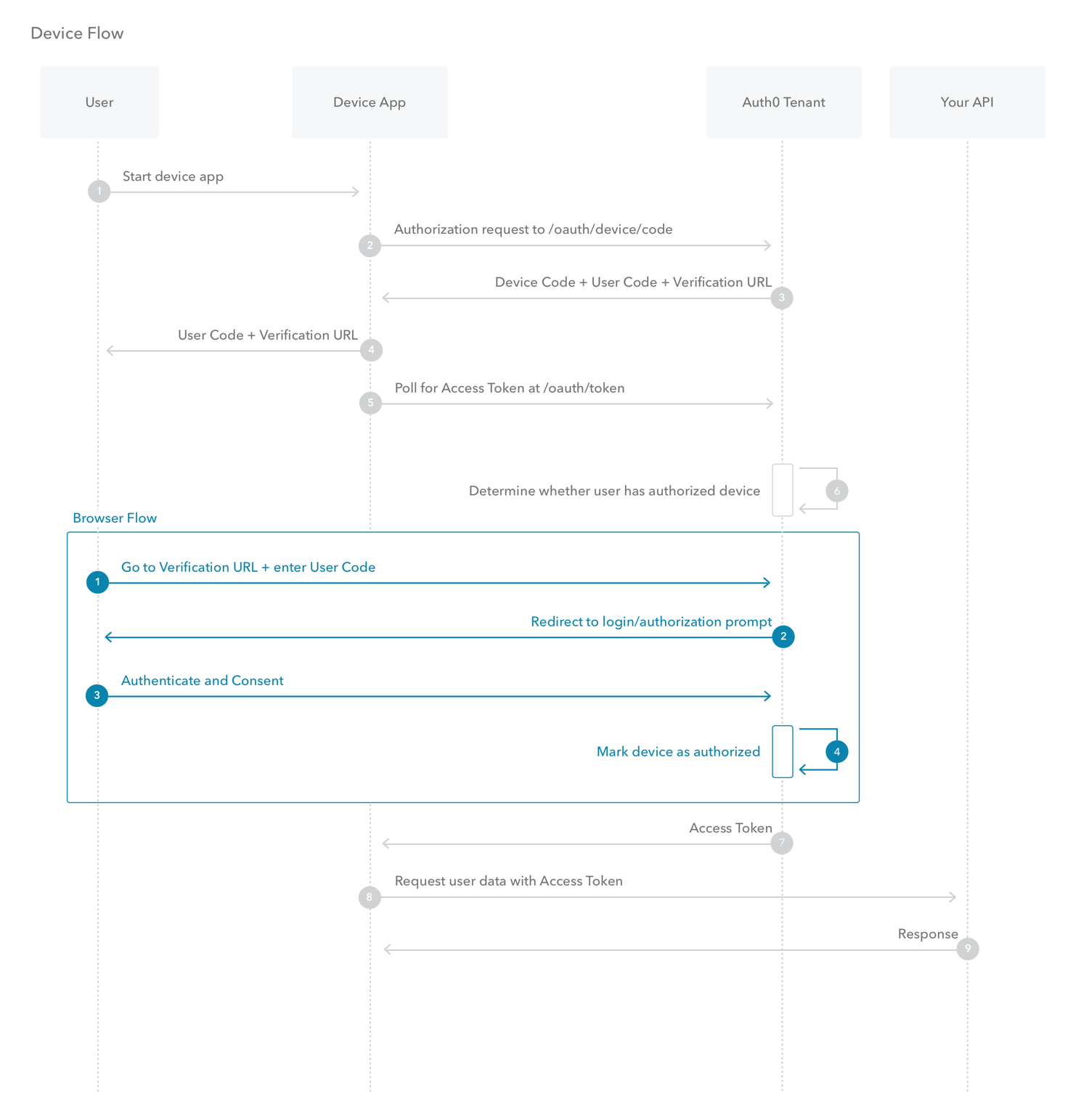
Device Authorization Flow
